CNS thought to introduce to its clients and prospects its latest network security solution known as SecurityScoreCard. This product aims to assist organizations to continuously assess their cyber risk via an easy to understand risk scoring.
The webinar was hosted on 14th October 2020, and was attended by more than 70 interested individuals who received a free securityscorecard report for their organizations!
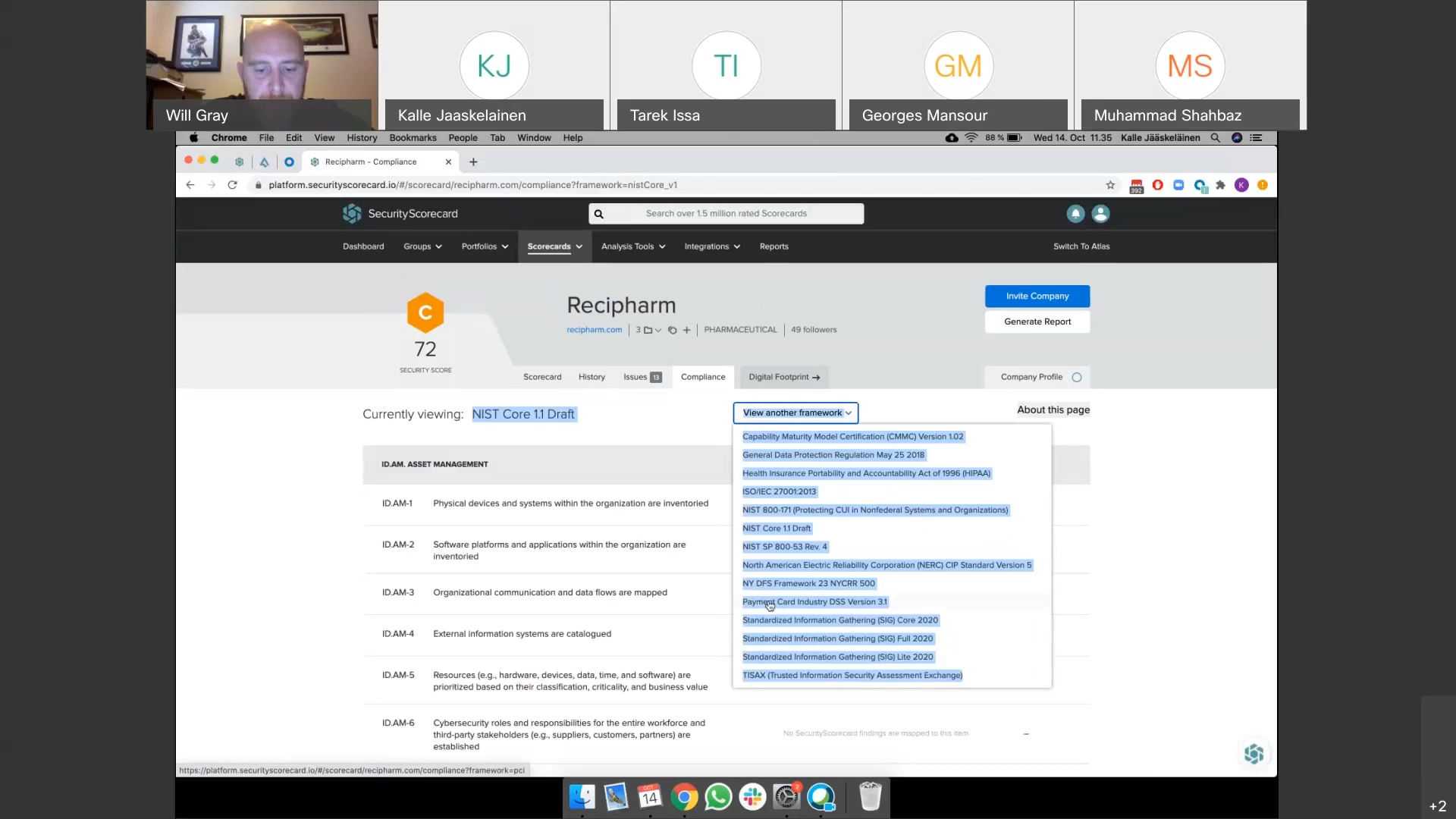
Will Gray Director, Sales at SecurityScorecard, Kalle Jääskeläinen, Sales Engineering at SecurityScorecard and Nizar Hirbli, Regional Solutions Engineer – GCC at Crestan introduced the Security Ratings Services (SRS) and its use cases to the attendees. They shed the light on how an IT department can communicate cyber risk to the board and reviewed several companies that were breached this year and discussed if it is possible to predict such breaches.
Here below you can find major take aways from our webinar:
- The importance of continuously assessing your cyber risk via an easy to understand risk scoring tool.
- Security Scorecard Ratings offer easy-to-read A-F ratings across ten groups of risk factors including DNS health, IP reputation, web application security, network security, leaked information, hacker chatter, endpoint security, and patching cadence.
- Security Scorecard Ratings evaluate an organization’s cybersecurity risk using data-driven, objective, and continuously evolving metrics that provide visibility into any organization’s information security control weaknesses as well as potential vulnerabilities throughout the supply chain ecosystem.
What is Security Scorecard Ratings?
Security Scorecard Ratings offer easy-to-read A-F ratings across ten groups of risk factors including DNS health, IP reputation, web application security, network security, leaked information, hacker chatter, endpoint security, and patching cadence.
SecurityScorecard Ratings evaluate an organization’s cybersecurity risk using data-driven, objective, and continuously evolving metrics that provide visibility into any organization’s information security control weaknesses as well as potential vulnerabilities throughout the supply chain ecosystem.